扫描后:
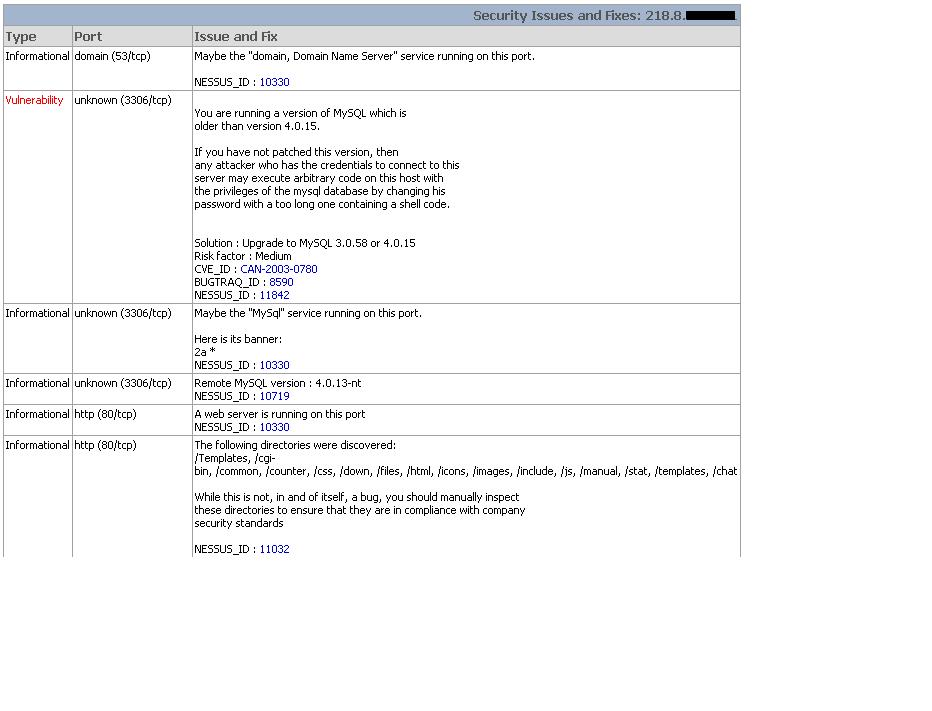
results|218.8.252.131|unknown (3306/tcp)|NOTE|Remote MySQL version : 4.0.13-nt;NESSUS_ID : 10719;
results|218.8.252.131|unknown (3306/tcp)|HOLE|;You are running a version of MySQL which is ;older than version 4.0.15.;;If you have not patched this version, then;any attacker who has the credentials to connect to this;server may execute arbitrary code on this host with;the privileges of the mysql database by changing his;password with a too long one containing a shell code.;;;Solution : Upgrade to MySQL 3.0.58 or 4.0.15;Risk factor : Medium;CVE_ID : CAN-2003-0780;BUGTRAQ_ID : 8590;NESSUS_ID : 11842;
results|218.8.252.131|http (80/tcp)|NOTE|The following directories were discovered:;/Templates, /cgi-bin, /common, /counter, /css, /down, /files, /html, /icons, /images, /include, /js, /manual, /stat, /templates, /chat;;While this is not, in and of itself, a bug, you should manually inspect ;these directories to ensure that they are in compliance with company;security standards;;NESSUS_ID : 11032;
results|218.8.252.131|http (80/tcp)|NOTE|The remote web server type is :;;Apache/1.3.28 (Win32) PHP/4.3.2 ;;;Solution : You can set the directive 'ServerTokens Prod' to limit;the information emanating from the server in its response headers.;NESSUS_ID : 10107;
summary|218.8.252.131|OS: Unknown OS; PORT/TCP: 21, 53, 80, 3306
|


 论坛用户
论坛用户
 论坛用户
论坛用户 论坛用户
论坛用户